 Setting up an SSL with DWScript Web Server (and other http.sys services like mORMot) is simple, and it’s cheap, free even thanks to StartCOM. Encryption is also pretty darn fast on recent Windows server versions.
Setting up an SSL with DWScript Web Server (and other http.sys services like mORMot) is simple, and it’s cheap, free even thanks to StartCOM. Encryption is also pretty darn fast on recent Windows server versions.
Here is a quick guide to get you started.
Getting a Certificate
You can get a certificate from various certification authorities, at various price and service levels.
 You can get a free Class 1 certificate from StartSSL, it’s valid for one year, but limited to a subdomain only. For instance if you get one for “secure.mydomain.com” it won’t work for “www.mydomain.com”. These certificates are intended for individuals and non-commercial usage, as they don’t mean the organization has been certified to exist. However, they’re good enough to secure the connection without any browser warnings.
You can get a free Class 1 certificate from StartSSL, it’s valid for one year, but limited to a subdomain only. For instance if you get one for “secure.mydomain.com” it won’t work for “www.mydomain.com”. These certificates are intended for individuals and non-commercial usage, as they don’t mean the organization has been certified to exist. However, they’re good enough to secure the connection without any browser warnings.
Once you’ve generated you certificate, you’ll want the PKCS#12 file from it (.p12), you can generate it from StartSSL ToolBox / Create PKCS#12 (PFX) File utility.
It goes without saying that your should be very careful with your certificate files and password protection for them. Feel free to use my passphrase generator for a strong password.
Installing the Certificate
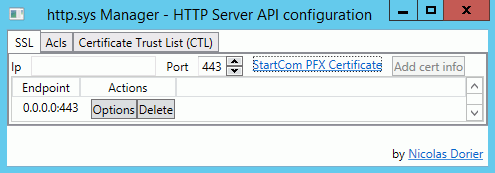
The simplest way to setup the certificate in Windows 2008 or 2012 for use with DWScript Web Server is to use HttpSysManager. Just download and unzip it.
Then in the first tab “SSL”, click “Select a certificate”, then pick your .p12 file, enter your password.
In the IP field, enter 0.0.0.0 if you want the certificate to work for all IPs on the machine, then click “Add cert info”.
Setting Up options.json
The minimal requirement for SSL support in the DWScript Web Server is to specify the SSL Port, which by default isn’t active, so you need to have in your options.json at least
{
"Server" : {
"SSLPort": 443
}
}
Restart the service if necessary. Done.



I wouldn’t trust StartCOM, the last time I checked they still generated your private key on their servers…
That’s not the only way, but they allow it for convenience:
http://security.stackexchange.com/questions/22680/where-does-startssl-generate-the-cerificate-server-or-client-side
That said, if they were to leak private keys, they would lose their certification authority status, and then browsers would report the connection as unsafe. So IMHO it’s safe to assume that they likely have better security than most web and sys admins do.
Of course, that doesn’t mean they don’t leak them to the NSA, but then again, the NSA may not need your private keys in the first place 😉